Reading time: 8 – 12 minutes

I wanted to make a high level secure WI-FI network, not like is
been made now with WEP and other foolishness. Then I installed a
FreeRadius server to work with a Linksys
WRT54G. The basic idea is to install a HyperWRT to the WRT54G
(Pof’d advice). After I configure it as WPA-Radius to the firewall were
I installed Freeradius. This
last step is optional because standard WRT54G firmware supports
WPA-Radius.
Network diagram; pay attention at the firewall and AP, the rest it
is not important:
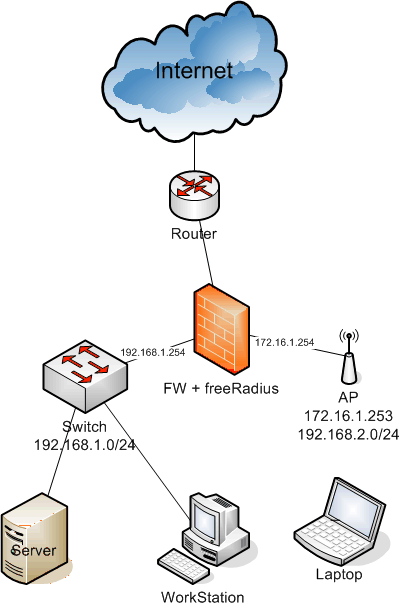
To configure everything I just follow the instructions from the 802.1x HOWTO.
Anyway I made a small guide:
- Install Freeradius in the firewall: emerge freeradius
- Configure Freeradius to work with EAP/TLS
- Generate certificates
- Check freeradius works propertly
- Configure the AP (Linksys WRT54G)
- Configure Windows XP with SP2 clients
- Configure Linux clients
The configuration files I used for freeradius are the next ones:
- /etc/raddb/radiusd.conf:
General Radius configuration file, we must define auth systems and
others to use. There are a lot of parts I haven’t used so I left it as
was coming. I want to thank Pof’s help on borrowing me his
configuration files in order to configure mines. - /etc/raddb/clients.conf:
IPs and network systems that can be radius clients; in our case the AP
(172.16.1.253).
Although the radius power, documentation and lack of time to
experiment gives you this, but if someone can do it better I would
apreciate to know it.
For the generation of certificates the idea is to made them from a
certified entity, but this only happens in films and big companies.
Let’s take OpenSSL and do our work.
If you still haven’t got it, you know: emerge openssl. Sure enough we
aren’t good at PKI and other similar things, then it is better to learn
using freeradius and openssl scripts, because with some modifications
we can create certificates to work with our secure wi-fi networks.
As I was saying wea re going to use the freeradius and openssl
scripts to generate certifieds, then first of all let’s go to the
freeradius folder were we can find a folder called “scripts” with:
CA.certs, certs.sh and xpextensions. I recomend checking order
locations inside scripts because I had problems with this. If you are
lazy to look at the files, you can check mine in this small package: certs.tar.gz
this files are modified to work from the same folder we are working in,
I recomend creating a new and empty folder. Once we have identified the
files, we must have in PATH the script CA.pl, that is a perl script,
but not many times is copied to the PATH so I copied to /usr/bin and I
deleted it after generating the certifieds. I also included the file in
the package, if you are lazy…
Once we have all things in a folder ready to work we can edit
CA.certs to include our information to the variables at the begining of
the file. There is no need to change more variables, it is done
automaticly. Don’t forget the password because we will need it when
configuring the server and the clients.
To generate the certifications just:
# ./certs.sh
and the output will be something like that:
Generating DH parameters, 512 bit long safe prime, generator 2
This is going to take a long time
........................+......................................................+...........+................................+..........+.......................+...+...........................................+...............................+............+..............+.................................+.......+..+.................................................+....+....................+.........................................+..+......+................................................+........+.....+...............+...........+.+..................+...........+..................................................+............+......+.+.................+.+.........................+....+................+....+....+.....+.........................+............+......+.+..........................................................+..+...........................................+.........................+.............................+..................................................+...+...++*++*++*++*++*++*
See the 'certs' directory for the certificates.
The 'certs' directory should be copied to .../etc/raddb/
All passwords have been set to 'whatever'
Don’t care about the messages, just in case any error happen. Now
you’ll have a new folder inside the folder were you are, called certs
and inside can find all the certifications for the server and the
client. I recomend coppying the contents from ./certs to
/etc/raddb/certs then you’ll not have to change the configuration files
I give you.
The most important thing now is checking the configuration files I
gave you first and check that the radius server starts without
problems, that unfortunately never happens. About the radiusd.conf I
don’t think you might have lots of problems, just check that paths to
the certifications are the correct ones you just have created. Also
check the parameter: private_key_password = whatever.
Change ‘whatever’ for your password, the one you have used for the
variable PASSWORD inside the CA.certs file. If you don’ do that, once
you start the daemon with radiusd -X you will be
asked for a key used to symetricaly crypt the files with a private key,
as is the password I am talking about. If you don’t do that when /etc/init.d/radiusd
start you’ll have an error because the server would not use
the keys to access the certifications.
Just do : radiusd -X and if you get the next
output:
Ready to process requests.
everything works fine. Just do CRTL+C and start the Gentoo daemon (/etc/init.d/radiusd
start)
or just leave it like it as it is in a terminal client then you can see
the logs been generated in order to check if everything works ok. If
you want to check the history logs while the daemon is on, just find
them at /var/log/radius/. The start daemon logs are
in startup.log and the connection ones in radius.log.
To see the log in real time just do: tail
-f /var/log/raddb/radius.log
Before configuring the users you need to configure the AP as
radius client. You can configure the AP as you want but I configured it
as a router between two networks; the user’s network with DHCP
(192.168.2.0/24) and the called Internet by the AP (172.16.1.253). I
like configuring this way the network; a cable that is going to the
firewall where can comunicate with the freeRadius. For example; the
firewall interface with IP 172.16.1.254 and the ‘Internet’ interface
from the WRT54G with IP 172.16.1.253. Then you need to make sure that
the IP is allowed to work with radius editing file /etc/raddb/clients.conf
like in the next example:
client 172.16.1.253/32 {
secret = SharedSecret99
shortname = localhost
}
See that here appears another password, this ‘pre-shared
key’ is used by the WPA-client (WRT54G) and the radius server
(freeRadius) to crypt their communications. Then you have to make sure
this key is inserted in the AP configuration. Here I am attaching a
screenshot of how the AP wireless security configuration must be to
work with radius server:
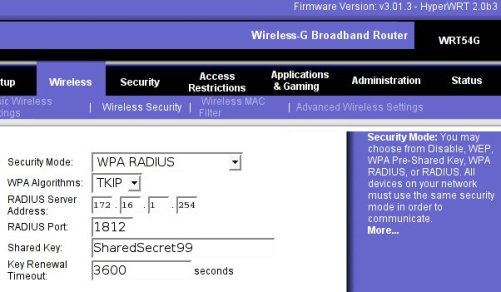
For the configuration of the Windows client first of all you have
to check if the wifi network card has the correct firmware to work with
WPA with EAP/TLS. If you don’t know it, just use the next manual of how
to configure a WXP and if you cannot find the options I show it is that
your card isnt’ valid. I just tryed in a WXP SP2, for all the rest, I
don’t know.
I made a PDF file with lots of screenshots to easy configure the
WXP client. You have to install two certification files; root.der
and root.p12. You should create them before and can
be find at /etc/raddb/certs.
I recomend you copying this files into a pendrive and use it for all
clients.
How
to install the EAP/TLS clients with Windows XP SP2 in PDF format.
This document is based in: HOWTO:
EAP//TLS Setup for FreeRADIIUS and Wiindows XP Supplliicant in PDF
format too.
About Linux configuration; I haven’t tryed yet because my PCMCIA
wifi card firmware is old. But I am going to try the card integrated in
my laptop that works with ndiswrapper or linuxant Linux drivers, both
of them prepared to use wap_suplicant, necessary for the WPA/TLS
authentication in a Linux box. When I get to the point don’t
worry, I’ll tell you. Don’t want to work much with Windows, I got
nervous at work seing that kaos.
I attach you some references I used to help me:
- 8021X-HOWTO
–
This document describes the software and procedures to set up and use
IEEE 802.1X Port-Based Network Access Control using Xsupplicant as
Supplicant with FreeRADIUS as a back-end Authentication Server. - FreeRADIUS/WinXP
Authentication Setup – This post describes how to build a
FreeRADIUS server for TLS and PEAP authentication, and how to configure
the Windows XP clients (supplicants). The server is configured for a
home (or test) network. - HOWTO on
EAP/TLS authentication between FreeRADIUS and XSupplicant – This
document describes how to setup strong cryptographic authentication
between XSupplicant and FreeRADIUS. This is accomplished using part of
802.1x authentication for wireless network. In particular it uses
EAP/TLS extension, and TLS handshake.
I pretend this helps as much people as possible. Thank you for
your patience.
0 thoughts on “Secure wi-fi Net : freeRadius + WRT54G = 802.1x (WPA-radius EAP/TLS)”
hi!
your manunal helped me a lot. it tryed to read your sample configs but the links does not work. could you send the sample config per email? my adress: ok@geeks.at
regards,
otto
Please try it, now.
Thank you.
i tried to download your certicficate…but its not valid…do you have the latest?
i would like to ask you a couples of questions:
1. in your client.conf your secret key is SharedSecret99 but in your radiusd.conf your private_key_password is whatever, is it ok to have different?
2. what is this mean "ippool main_pool {
range-start = 192.168.1.4
range-stop = 192.168.1.254
netmask = 255.255.255.0
cache-size = 800
session-db = ${raddbdir}/db.ippool
ip-index = ${raddbdir}/db.ipindex
override = no"?
3. is your radius connected to database to store the user and password list?
im sorry to ask you a lot of questions, its just im doing my thesis to build a radius server and the access point is wrt54g also…but it doesnt work, and my deadline is coming up.will you help me?
ad_recv: Access-Request packet from host 192.168.1.1:2061, id=0, length=166
User-Name = "linksys"
NAS-IP-Address = 192.168.1.1
Called-Station-Id = "0014bf04a514"
Calling-Station-Id = "000e3574ca4d"
NAS-Identifier = "0014bf04a514"
NAS-Port = 51
Framed-MTU = 1400
State = 0xb23b333336fba1b91206537df02cd417
NAS-Port-Type = Wireless-802.11
EAP-Message = 0x020300210d8000000017150301001208f9e73fcdfba3b0ed5dd3c41101dd967eb1
Message-Authenticator = 0xc0f6b9b2c301f8a7f362abe41fad9227
Processing the authorize section of radiusd.conf
modcall: entering group authorize for request 27
modcall[authorize]: module "preprocess" returns ok for request 27
rlm_eap: EAP packet type response id 3 length 33
rlm_eap: No EAP Start, assuming it's an on-going EAP conversation
modcall[authorize]: module "eap" returns updated for request 27
rlm_realm: No '/' in User-Name = "linksys", looking up realm NULL
rlm_realm: No such realm "NULL"
modcall[authorize]: module "realmslash" returns noop for request 27
rlm_realm: No '@' in User-Name = "linksys", looking up realm NULL
rlm_realm: No such realm "NULL"
modcall[authorize]: module "suffix" returns noop for request 27
users: Matched entry DEFAULT at line 96
modcall[authorize]: module "files" returns ok for request 27
modcall: group authorize returns updated for request 27
rad_check_password: Found Auth-Type EAP
auth: type "EAP"
Processing the authenticate section of radiusd.conf
modcall: entering group authenticate for request 27
rlm_eap: Request found, released from the list
rlm_eap: EAP/tls
rlm_eap: processing type tls
rlm_eap_tls: Authenticate
rlm_eap_tls: processing TLS
rlm_eap_tls: Length Included
eaptls_verify returned 11
eaptls_process returned 7
rlm_eap_tls: Received unexpected tunneled data after successful handshake.
rlm_eap: Handler failed in EAP/tls
rlm_eap: Failed in EAP select
modcall[authenticate]: module "eap" returns invalid for request 27
modcall: group authenticate returns invalid for request 27
auth: Failed to validate the user.
Delaying request 27 for 1 seconds
Finished request 27
Going to the next request
Waking up in 6 seconds…
— Walking the entire request list —
Sending Access-Reject of id 0 to 192.168.1.1:2061
EAP-Message = 0x04030004
Message-Authenticator = 0x00000000000000000000000000000000
Cleaning up request 27 ID 0 with timestamp 43dc0fa0
i still cannot login from my laptop..i followed your steps…
thats the message on the server, do you know why?
if you dont mind, would you sent me your whole conf file? just the raddb folder would be help me a lot…
thx man
[3] my certificate is out of date from 25th of January. If you wanna another certificate please make your own like is indicated in this post. If you have any problem in the process may be I can help you.
[4]
1. isn't the same password, whatever is a symetric password to access to certificate. SharedSecret99 is the password to establish a secure path over local network to connect my AP to my RADIUS server.
2. if you look in default configuration file (radiusd.conf) you can see this information about this part of config file:
# Do server side ip pool management. Should be added in post-auth and
# accounting sections.
#
# The module also requires the existance of the Pool-Name
# attribute. That way the administrator can add the Pool-Name
# attribute in the user profiles and use different pools
# for different users. The Pool-Name attribute is a *check* item not
# a reply item.
3. my passwords are stored in plain text file (/etc/raddb/users)
[6] my /etc/raddb folder is by default except my radiusd.conf and clients.conf, that files are attached in this post.
Maybe you have a problem with you radius version I only tried my configuration with this version:
radiusd -v
radiusd: FreeRADIUS Version 1.0.5, for host , built on Oct 1 2005 at 18:22:05
Copyright (C) 2000-2003 The FreeRADIUS server project.
There is NO warranty; not even for MERCHANTABILITY or FITNESS FOR A
PARTICULAR PURPOSE.
You may redistribute copies of FreeRADIUS under the terms of the
GNU General Public License.
For more information about these matters, see the file named COPYRIGHT.
If you install this version of radius and re-generate your certificates. It works sure then the problem only can be your firmware in AP or your client configuration.
im sorry to message you this much, coz i really2 need help.
after you saw my log, you probably notice this:
rlm_eap_tls: Received unexpected tunneled data after successful handshake.
rlm_eap: Handler failed in EAP/tls
rlm_eap: Failed in EAP select
do you know what and why is that?
do want me to show you my radiusd.conf, users.conf, clients.conf, eap.conf files?
my radius version is 1.02..is that ok?
I'm looking for your error message in goolge and I found this (solution) Received unexpected tunneled data after successful handshake. As I said before you have a problem with your certificates.
Your radius version is older than mine, I don't know if your version has any important diferent working with certificates. Maybe upgrade your version to 1.0.5 is a good idea.
IMHO you have not to modify your config files only upgrade version of radius and try it, then if it doesn't work regenerate your certificates like my post or like EAPTLS.pdf document.
Good luck
many times i tried to generate my certificate but its always not valid. the message was digital signature is not valid and the last time i tried the certificate is not valid.
do you have any idea what is wrong?
should i download and install the hyperWRT?
what is your firmware? as you can see in the post my firmware is hyperWRT 2.0b3
thx to you, now my radius is working.but when my laptop trying to connect, the radius didnt ask about username and password. the radius only check the certificate. how to make login window pop up on my laptop…and the radius will check if it is a correct login and password or not?
[15] My auth system works as you say, but if you want an user authentication you need to modify a little your radiusd.conf file. If you want you can try to use EAP/TTLS insted of EAP/TLS it supports users authentication, accounting and anything else.
Now I don't remember all you need to do user authentication because I configure it for 1 year ago. And I don't have this details now. But if you get this please send me this information to extend my post.
hello…my radius is running perfectly…but the radwho is empty….any idea why?
milieu etrange http://www.milieu-etrange.0chattes.com [URL=http://www.milieu-etrange.0chattes.com]milieu etrange[/URL]
Hi people i´m from chile your how to was great I spent lot of time trying to find a good how to. sorry about english bye
[URL=http://yooukenv.com]zbcofxmj[/URL] huvfptce jfhaclmt http://ivzuzguk.com omzgooaf eggkhbwj
Hi,
My questions.
1) Why do you need to upgrade the firmware in the AP? Can you just use an unupgrade AP?
2) How can i make the radius accepts certificate and mac address for authentication?
[21]
1) It's not necessary upgrade the firmware. I upgrade it for other reasons, like access to AP via telnet or SSH.
2) IMHO it's not possible to authenticate the AP with Radius via Certificate and MAC.
I follow your guide but i got an error in WXP (system event viewer).
"The certificate received from the remote server was issued by an untrusted certificate authority. Because of this, none of the data contained in the certificate can be validated. The SSL connection request has failed. The attached data contains the server certificate."
My radius keep sending a access-challenge.
What exactly i miss? Is it problem with the certificate? I use freeradius in Fedora core 9.
How can i solve this problem?
[23]
Are you installed root certificate of certificate authority?
Yes, exactly what u wrote in this step.
I tried to find someones tutorial and i found that somes use root.der and cert-clt.p12. But you use root.de and root.p12 in WXP.
So, whats the different? Does it effect my authetication session?
[25]
It's the same root.der is the root certificate of Certificate authorithy and root.p12 is a client certificate. You can see my cookbook for EAP-TTLS maybe it can help you: cookbook eap-ttls
Suddenly, i successfully configure radius to accept WAP+EAP TLS authentication. I dont know how. Just followed your steps you gave.
The problem now is, the authentication only depend on EAP. How can i make a control access for the users that listed in users file and SQL? I failed to do this.
[27]
If you want authenticate user you need TTLS no TLS. You can see this: Securing wi-fi net with EAP/TTLS it is a wiki entry but If you need help you can ask me all you want because I write this cookbook.
My next problem, if you dont mind.
User authentication is a success. But any invalid authentication, freeradius still accept. How can i reject invalid or unauthorize user. I tried both on file and sql, but failed. Help me. Hope this is the last. 🙂
[29]
What is your WPA supplicant client? IMHO this a problem of a WPA supplicant it is not a problem of server. You can trace authorization via log file.
I think my problem is the same with Satrio (above). Its only checked certificate. It checked username but wether its valid or not, the system still aceept it because of the certificate. Im using XP supplicant SP1 with wifi patch.
[31]
You need third party supplicant XP doesn't support TTLS itself. Your problem is that only is only working your TLS part not TTLS. You doesn't request your PAP or CHAP auth because Windows doesn't require it.
GREAT! It is a success. I used SecureW2. Works fine.
1 more thing, i also like to validate the mac address along with username, so how can i write ni "users" and "sql"?
[33]
I don't know how can you validate MAC address too. I never do that.
Oriol, meet u again.
I successfully configure radius for EAP/TTLS. What i did was using SecureW2 as a supplicant. I set it to authenticate the username and validate the MAC address.
I tried to make security testing. I removed the certificate in the client (XP) and made the wifi connection again. The connection was a success.
In theory, the wifi connection also involve certificate to authenticate. So, without certificate, authentication will fail. Am i right? It seem like my client dont need any certificate. What to make radius server reject client that not has certificate?
[35]
I don't know what is your problem, because I don't use windows. In my linux boxes when I remove client certificate it doesn't work. May be you have a mistake in your radiusd.conf file…
Is it possible to include in freeradius configuration checking mac adress (not in WRT54)?
[37]
May be, but I never find it.
[url=http://blog.ccidnet.com/blog-htm-do-showone-uid-71719-type-blog-itemid-246811.html…]Çå³ýÍøÉϸºÃæÐÅÏ¢[/url]
[url=http://blog.19lou.com/10698179/action-viewpro…]Çå³ýÍøÉϸºÃæÐÅÏ¢[/url]