Network traffic sniffing: tcpdump on Linux + Wireshark on Windows
Reading time: 2 – 2 minutesFrom the Windows box using the CLI console (cmd):
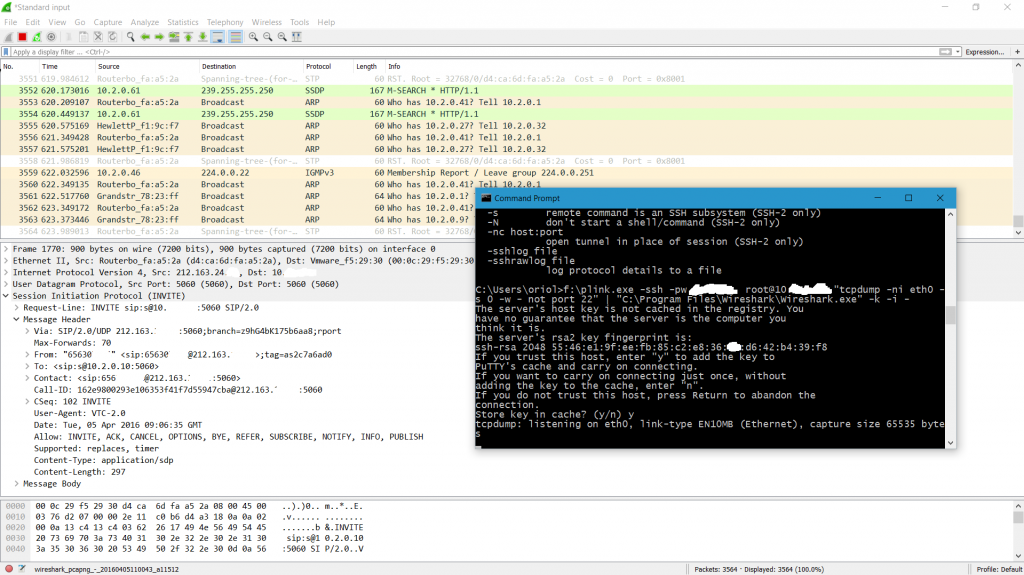
ssh USER@HOST "tcpdump -s 0 -U -n -w - -i NETIF FILTER" | "c:\Program Files\Wireshark\Wireshark.exe" -k -i -
# USER - remote user of the linux box
# HOST - host address of the remote linux box
# NETIF - network interface to snif in the remote linux box
# FILTER - (optional) rules for filtering traffic to capture
Use case:
C:\Windows\System32\OpenSSH>ssh root@192.168.4.74 "tcpdump -s 0 -U -n -w - -i eno2 udp and not port 53" | "c:\Program Files\Wireshark\Wireshark.exe" -k -i -Let me present a rare use case of this useful trick. I use a QNAP NAS as a gateway in my home network, where I have 5 NICs. So it’s really useful to snif traffic remotly but I have no tcpdump packet in the system. What I did is use tcpdump as Docker container and finally the commands is like that.
# sniffing SIP traffic (port 5060) on interface eth0
# remote linux host (QNAP NAS) use SSH port 55222
# docker container is created and when work is done is removed
C:\Windows\System32\OpenSSH>ssh -p 55222 admin@10.2.0.1 "cd /share/Container/tcpdump && docker run --rm --net=host corfr/tcpdump -s 0 -U -n -w - -i eth0 not port 22 and port 5060" | "c:\Program Files\Wireshark\Wireshark.exe" -k -i -