2016/09/01
1 comentari
Reading time: 2 – 3 minutes
At the beginning of August I’ve received a new home server, I decided to stop my old HP ML110 G5 and substitute that by a new silent and low power server also based on Intel technologies in this case it’s al i5 with 8G of RAM and 128GB of SSD for less than 300€ including custom costs I think it’s a very good investment.
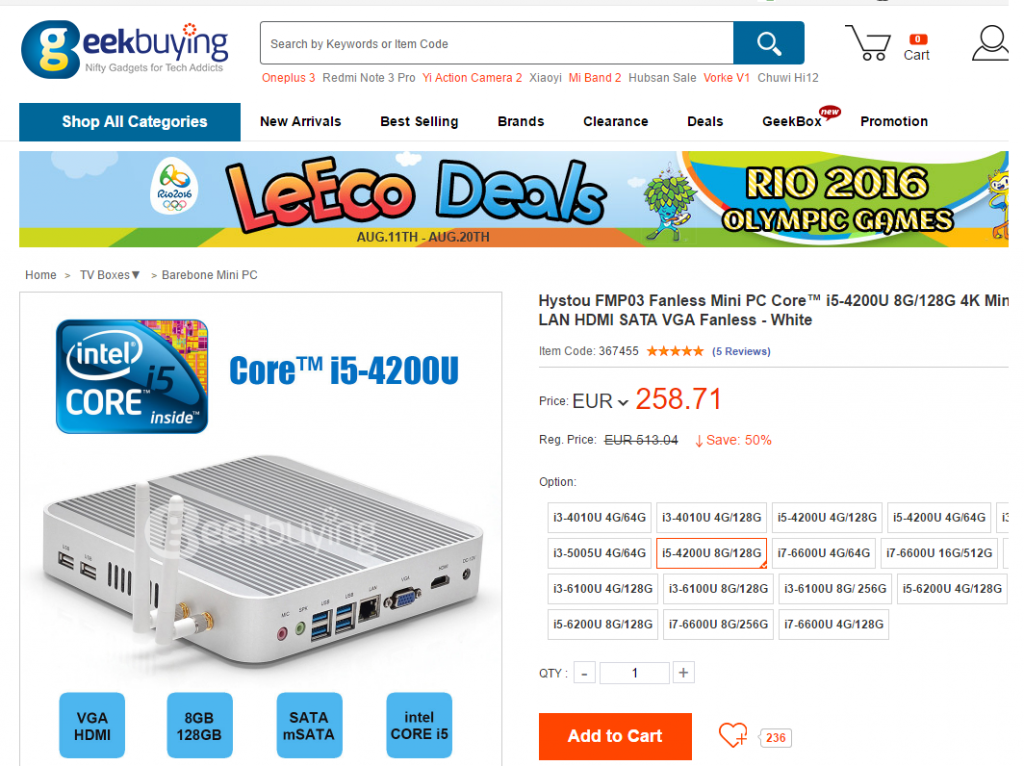
I installed Ubuntu 16.04 LTS server, I don’t tried de Win10 pre-installed. I happy to see a very new and powerful BIOS with tons of options. But in this blog entry I want to explain how to set-up the wifi card as a wifi AP. I didn’t have to do anything to configure the card. It worked by default.
Ralink corp. RT3090 Wireless 802.11n 1T/1R PCIe
The first thing is check if the wifi network is compatible with the AP mode.
iw list
...
Supported interface modes:
* IBSS
* managed
* AP
* AP/VLAN
* monitor
* mesh point
...
Next thing is install the “hostapd” which is going to take care to set-up the AP. The configuration file have to be something like that “/etc/hostapd/hostpad.conf
interface=wlan0 # change that with the wifi interface name
driver=nl80211
ssid=test # your wifi network name
hw_mode=g
channel=1 # look up for a free channel
macaddr_acl=0
auth_algs=1
ignore_broadcast_ssid=0
wpa=3
wpa_passphrase=1234567890 # passwor to join the wifi network
wpa_key_mgmt=WPA-PSK
wpa_pairwise=TKIP
rsn_pairwise=CCMP
Modify “/etc/default/hostapd” and put that:
DAEMON_CONF="/etc/hostapd/hostapd.conf"
Start the hostapd service:
sudo service hostapd start
Now the AP is running but a DHCP service giving IPs it’s need, I used “isc-dhcp-server”. First thing to configure is “/etc/default/isc-dhcp-server” with the wireless network name:
INTERFACES="wlan0"
Next file to be configured is “/etc/dhcp/dhcpd.conf”:
ddns-update-style none;
log-facility local7;
subnet 192.168.1.0 netmask 255.255.255.0 {
range 192.168.1.128 192.168.1.253;
option domain-name-servers 192.168.1.1;
option routers 192.168.1.1;
}
Don’t forget to start the service:
sudo service isc-dhcp-server start
If it’s needed remember to create the proper iptables rules and enable “ip_forward” in /proc filesystem. I’m not going to describe that because in my case it’s not going to be useful.
This is not a specially interesting post entry but useful as a reference, when you have to use a fast and easy cookbook to setup a wifi AP.
 Yesterday I found a tool called
Yesterday I found a tool called  Some weeks ago I finished
Some weeks ago I finished