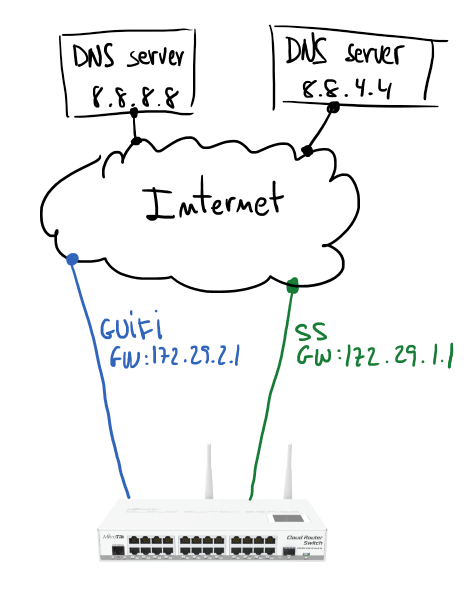
Based on my home configuration I’m going to describe how to set up a Mikrotik to manage fail over Internet connection. Next schema describes a Mikrotik gateway with two internet connections (GUIFI and SS). Assuming GUIFI as a default Internet connection periodic checks on Google DNSes (8.8.8.8 and 8.8.4.4) will allow to know when it’s good to change the default route.
If you have some Linux routing background it will be easier to understand the configuration. Main idea is use policy routing tables and mark packets to use one table or other. In my case I have two routing tables GUIFI and SS, and of course, the default gateway of each of those tables is the gateway indicated in the schema.
First step is take care about the routes for hosts to monitor; using GUIFI connection will be checking connectivity to 8.8.8.8 and using SS the monitored host will be 8.8.4.4.
/ip route add dst-address=8.8.8.8 gateway=172.29.2.1 scope=10 add dst-address=8.8.4.4 gateway=172.29.1.1 scope=10
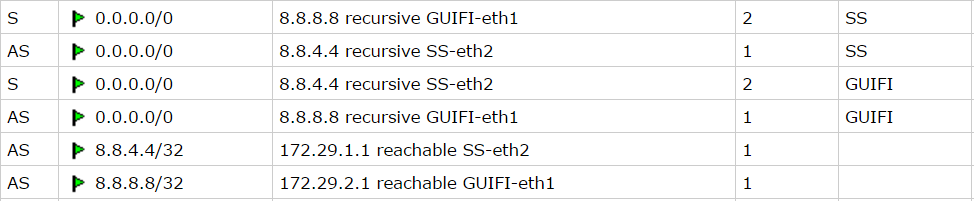
Second step is configure two routing tables, those routes will check Internet hosts availability. Routes are resolved recursively (more info), and will be active only if any host is pingable.
# routing table for GUIFI /ip route add distance=1 gateway=8.8.8.8 routing-mark=GUIFI check-gateway=ping add distance=2 gateway=8.8.4.4 routing-mark=GUIFI check-gateway=ping # routing table for SS /ip route add distance=1 gateway=8.8.4.4 routing-mark=SS check-gateway=ping add distance=2 gateway=8.8.8.8 routing-mark=SS check-gateway=ping
Routing table looks like that:
Next step will be create marking rules in the firewall:
# next rule mark all LAN traffic (10.2.0.0/26) before routing # it'll be processed by routing table GUIFI # it makes GUIFI the default Internet connection /ip firewall mangle add action=mark-routing chain=prerouting comment="All LAN traffic" dst-address=\ !10.0.0.0/8 new-routing-mark=GUIFI passthrough=no src-address=10.2.0.0/26
If any specific host, service or whatever want to use specific routing table, then you can create new rules with proper mark to redirect the traffic to that Internet connection. But if that path fails other Internet connection will be used.
In my case I have a more complicated scenario, internal VoIP server uses a IP Telephony service only available through GUIFI connection. The way to force that is forbidding traffic to SS connection. A simple firewall rule will help to do that:
# X.X.X.X = IP address of the IP telephony provider /ip firewall filter add action=reject chain=forward dst-address=X.X.X.X in-interface=\ bridge-lan out-interface=SS-eth2
I hope previous simple notes are useful for you, they are inspired by Advanced Routing Failover without Scripting.
2 thoughts on “Internet fail over connection with Mikrotik”
Thanks for this how to. I have a problem. After i create this route the internal mikrotik service (es l2tp client, dns) don’t work. Any suggestion? Thanks
No idea, sorry.
Comments are closed.