Restricted user for SSH port forwarding
Reading time: 7 – 11 minutesI love “ssh -R” reverse SSH is really useful when you have to get access to a Linux machine behind a NAT or firewall. One of the most powerful scenarios to get that running is use a third machine with a public IP address. The idea will be run reverse SSH command in target Linux and publish a forward port at the third server, so you only have to connect to a published port in that third server and you’ll get the target Linux thanks to the reverse SSH connection open between them.
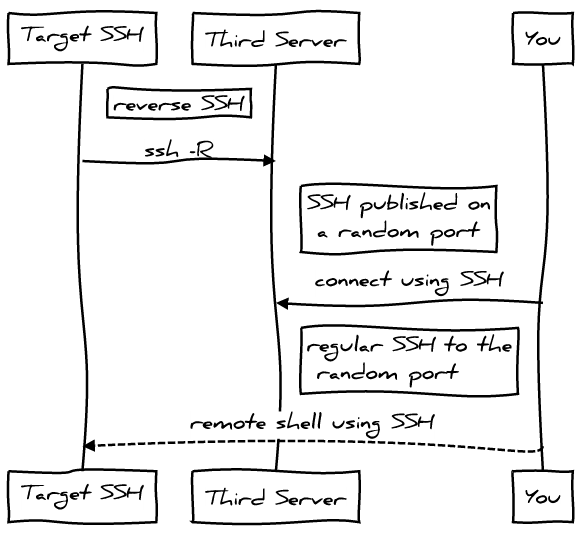
A long time ago I talked about that in my podcast “2×04 SSH avançat“.
With this scenario we have a security challenge with the SSH user account on the “third server”, we want a secure user:
- without shell and sftp access
- secure enough to only allow port forwarding features
- access only allowed with authorized keys
I’m not going to give precise Linux instructions on that limited user, but for user you’re not going to have problems to get that:
/etc/passwd(-):
limited-user:x:1001:1001::/home/limited-user:/etc/shadow(-):
limited-user:!:17037:0:99999:7:::/etc/ssh/sshd_config:
Match User limited-user GatewayPorts yes ForceCommand echo 'This account can only be used for maintenance purposes'
Of course, you’ll have your own UID, GID and use your own username. And at “/home/limite-user/.ssh/authorized_ssh” you’ll have to pub public key of the clients that want to use the service.
I’ve got my inspiration to get that from: How to create a restricted SSH user for port forwarding?. Thank you askubnutu.com.